A common belief in the cybersecurity world is that there are two kinds of companies: Those that have been hacked and those that don’t know they’ve been hacked. Cybersecurity is an essential part of doing business these days, and one standard tool to keep hackers at bay is encryption.
Encryption lets you protect data you send, receive, and store, regardless of device, and involves altering text to make it virtually impossible for cybercriminals to read. The text is essentially made to be unreadable, and only those who have a decryption key can decipher it. It is a must-have for your business, as it allows your employees to safeguard their passwords and other sensitive information against cybercriminals.
This approach can protect Social Security numbers, bank account information, and other critical data against cyberattacks. Even if hackers steal data that has been encrypted, they still won’t be able to use it without a decryption key.
This guide explores the importance of encryption for today’s businesses. It also explains how to secure data across your company.
How Does Data Encryption Work?
Encryption allows a business to scramble data into an unreadable format, i.e., “cipher text.” It protects the confidentiality of information stored on a company’s computer systems or transferred between its employees and customers across the internet. Here’s what to know:
- A company can scramble data to restrict access to data on computers, hard drives, smartphones, tablets, and other devices.
- An encrypted device that has been lost or stolen faces minimal risk of data misuse by anyone lacking the decryption key.
- Employees can also make text unreadable when sharing emails or other messages with one another or customers.
- This ensures only authorized recipients can read them, enabling employees to share information with colleagues and customers securely.
Businesses can take solace in using an extra layer of protection to keep their data safe. They can even use different types of encryption to safeguard information across all departments.
Types of Encryption
There are two types of systems for scrambling data: symmetric and asymmetric. Symmetric is perhaps the most straightforward option to make data unreadable to cybercriminals. It involves the use of a single password to encrypt or decrypt data.
Businesses can use the asymmetric option to set up keys for encryption (public) and decryption (private). The public key is shared among all business users and lets them scramble any data they choose. The private key is used exclusively to decrypt data; this key is generally not shared among all users.
Encryption Standards
It helps to understand how businesses use encryption to verify that their data is protected against cyberattacks. Here are five standards that companies frequently use to ensure their encryption strategies are up to date.
1. Triple Data Encryption Standard (DES)
DES was established in 1977, but plenty has changed in security since. Many businesses still rely on triple DES, which involves encrypting data, then decrypting it, followed by encrypting the information once again. This offers at least three times the protection of the initial standard.
2. RSA
RSA is a popular option for secure data transmission. It leverages a strong algorithm for scrambling data.
3. Advanced Encryption Standard (AES)
AES dates to 2002. The U.S. government established it to help companies worldwide make their data unreadable to cybercriminals.
4. Twofish
Companies can take advantage of the Twofish algorithm for hardware and software encryption. Twofish offers a key size that ranges from 128 to 256 bits and is optimized for 32-bit CPUs. It is also unpatented, unlicensed, and available free of charge.
5. Secure Sockets Layer (SSL)
SSL is a top choice for safeguarding website data. It lets users make data unreadable as it travels to and from a site.
A business can scramble its data, but doing so won’t stop cybercriminals from trying to steal it. Companies that stay proactive in their efforts to safeguard their information against cyberattacks are well-equipped to minimize the risk of data theft.
6 Tips to Make Your Data Encryption Strategy as Strong as Possible

A data encryption strategy provides an excellent starting point for companies that want to secure their information. It requires a business to consider the information it manages and stores and who needs access. The company can then decide on a standard to safeguard its data, develop and execute its strategy, and monitor its results.
Encrypting data is an ongoing endeavor since cybercriminals are constantly searching for ways to steal information from businesses. Here are six tips to help you continuously enhance your data encryption strategy.
1. Use the Maximum Key Length
When it comes to key length, err on the side of caution. The longer the key length, the less likely it becomes that a cybercriminal can decrypt your data.
2. Take a Layered Approach
Use multiple layers to make an entire database unreadable to cybercriminals. This involves scrambling each element in a database individually. This can cause cybercriminals to give up on accessing your data, as it may take them many hours or days to do so.
3. Keep Your Keys Secure
Do not store your keys in a public cloud. You should instead use a system that lets you maintain complete control of access to your keys.
4. Verify the Implementation Process Is Completed Correctly
Perform an audit to verify that data is secured as expected. Address any implementation issues immediately. And conduct ongoing assessments to confirm that your information is protected 24/7.
5. Avoid Outdated Standards
Keep an eye out for new standards relative to encrypting data. AES, RSA, and Twofish are among the most popular options available today, and they are proven to help businesses secure their information.
6. Use a Digital File Shredder
Use a digital file shredder to delete unwanted files from your computer. You can then secure files that you want to keep on your device.
Be proactive as you use encryption and other security techniques and tools to guard against cyberattacks. If you need help along the way, seek out assistance from a cybersecurity expert.
Contact the Experts in Digital File Shredding
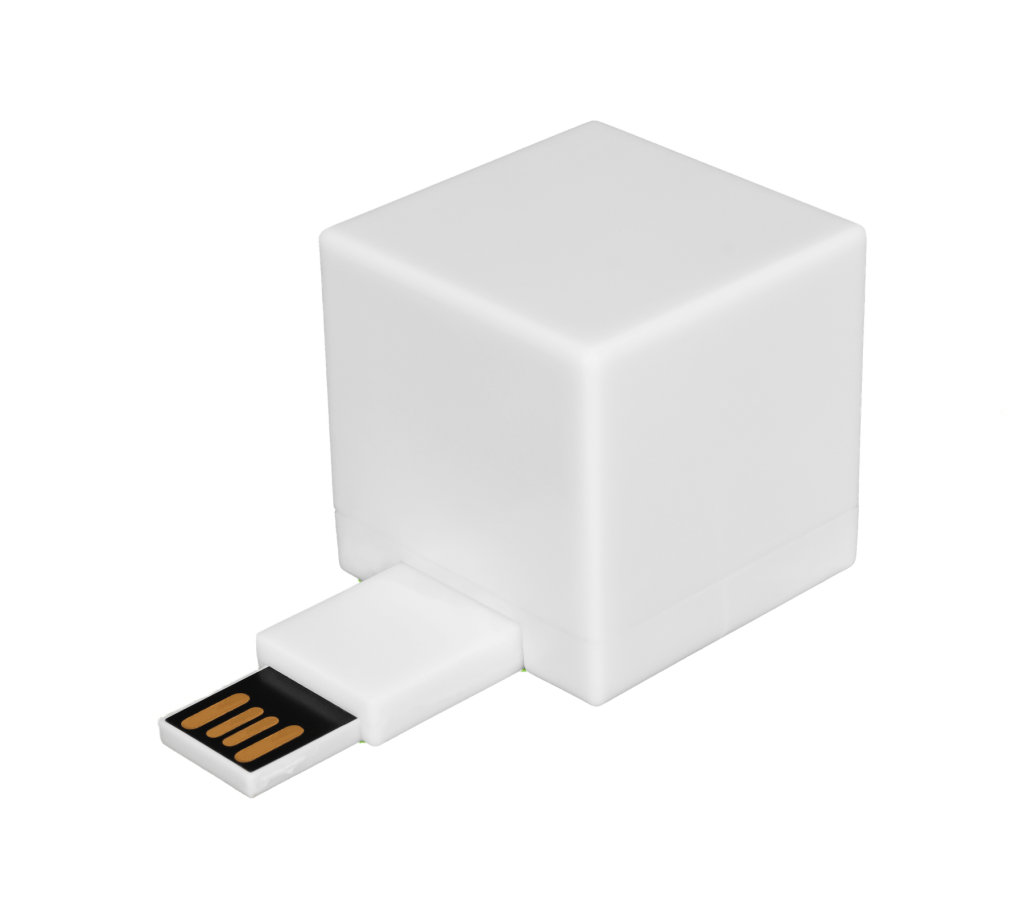
Every business, regardless of size or industry, can benefit from taking extra steps to protect their data – including shredding unneeded files before they get stolen. Shred Cube offers a USB file erasure device that you can use to remove files from a computer permanently.
Our innovative design allows you to drag-and-drop files, find duplicate files, and get rid of data so no one can get their hands on it. Contact us today for more information about our digital file shredding solution.