How much sensitive information is stored on your computer?
Once upon a time, I didn’t worry much beyond the couple of racy photos I let my old flame snap. What if they were to fall into the wrong hands—like the ones belonging to my new flame? But nowadays, my digital records tell a much more detailed—and potentially dangerous—story than a couple of indiscreet pictures could ever reveal.
From tax returns to bank statements to medical documents, our personal and business lives are laid out now in ones and zeros, often across multiple devices.
Cyber-criminals are becoming craftier and more villainous all the time, rendering individuals and companies more vulnerable than they ever were before.
While some files, like credit card records, may be a more lucrative target for nefarious hackers, all businesses have a responsibility to protect any personal information they collect from customers and a vested interest in protecting their own data.
You Need a Full-on Cyber-Safety Strategy
Safeguarding our own and our clients’ data takes careful planning, specialized tools, and above all, vigilance. It’s not a set-it-and-forget-it kind of thing.
And you need to build your strategy from the ground up. From installing the most sophisticated malware apps on individual PCs—and keeping them updated—to choosing the most safety-savvy ISP, there are dozens of small steps along the path to robust data protection.
Cybercriminals approach their job and your business from many angles. That’s why you need to adopt a broad perspective and include such schemes as password stealing, phishing, and ransomware in your purview.
And if you think that as a small business, you’re less likely to be a target of cybercrime, please don’t lull yourself a false sense of security. Some 43% of all cyber-crimes are perpetrated on small companies. And that may be due precisely to the fact that they are unprepared to defend themselves.

Coronavirus Complications
With many more employees working from home to comply with stay-at-home orders aimed at stopping the spread of COVID-19, some employers may be faced with securing locations outside their headquarters for the first time.
If you’re among them, it’s time to take a close look at where your data is traveling and how. Unless you take specific steps to protect them, every remote PC represents a separate security risk.
With so many individual threads connecting your business, it’s clearer than ever why they call it a web. Prudent companies will make cyber-safety a topic of both their onboarding processes and mandatory continuing education for all employees.

Put Yourself and Your Company on a Shred Schedule
Think of cybersecurity as you might think of dental hygiene. You need to attend to the basics, brushing and flossing, every day. But a couple of times a year, a professional cleaning is in order.
What does cleaning mean in the context of cybersecurity? It means getting rid of data you no longer use, need, or in some cases shouldn’t be storing by law. It’s important to stay on top of new regulations governing privacy. Many require businesses to delete certain records within mandated time frames.
If you work in the health care industry, for example, you’re charged with many serious responsibilities. You’re legally required to retain patient files for seven years. But protecting your data during that period is only part of the job. In 2019, some 25 million patient records were compromised in the US alone.
Deleting the records of inactive patients is the second step you must take to protect your patients’ data and shield yourself from liability claims should your organization suffer a data breach.
What if you run a business, like a manufacturing firm? You may not be legally responsible for deleting old files. But nor do you want the formula for your secret sauce stolen by an unscrupulous competitor. The same goes for employee records which contain confidential information, from I-9 forms to background check reports.
There’s a whole subsection of attorneys who make their livings representing employees (and employers) in legal cases involving breached files. And you don’t need the headache of litigation.
Deleted is a Relative Term
From a cybersecurity perspective, your computer’s trash or recycle bin is something of a false promise. Now you don’t see it. Later someone else might, even if you regularly empty the “receptacle” you have on your desktop. When you delete files, they may be hidden from view.
But they are entirely recoverable by anyone with the skills to find them. That includes any technically-trained thief who might break into your home or office. The files you name and save have many, behind-the-scenes tentacles attached to them that don’t show up in any visible folders. And hackers know how to find and follow them, right back to the data you thought you removed from your hard drive.
Private citizens—also known as your customers—are rightfully concerned about credit fraud or identity theft and they will hold businesses responsible for the damages they suffer should the data you store be compromised.
That’s why permanently and indelibly deleting files that contain clients’ personal information—along with the invisible data connected to them—is an important goal. But you don’t need to be a computer geek to reach it.
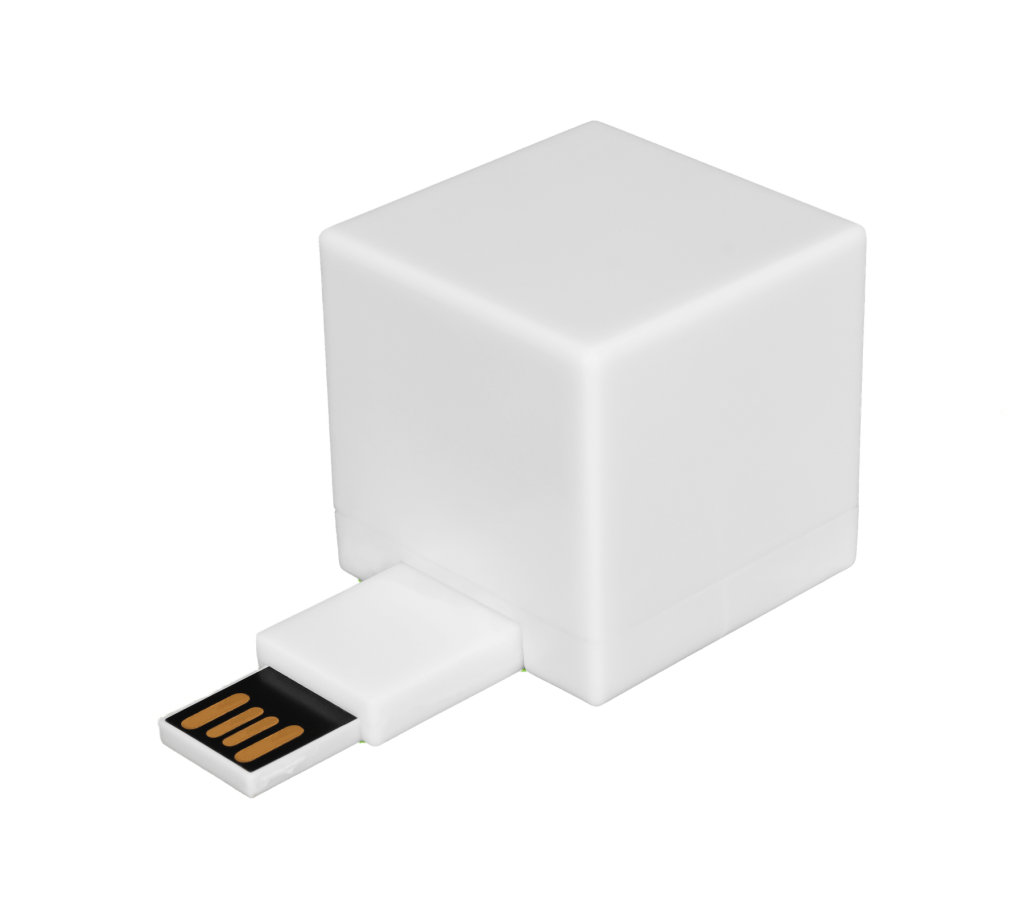
Fortunately, there’s a simple-to-use tool that will do it for you. It’s called The Shred Cube. Shred Cube fits in the palm of your hand. It’s plug-and-play-, drag-and-drop-easy to use. And it’s continuously being improved in response to new cyber threats. Updating it is free and fast, too, through our secured servers.
To learn how Shred Cube can help protect you or your business, give us a call at 866-346-6986. You can also speak to us via live chat or FaceTime. We’re here when you need us to answer your questions now and provide support once you’ve become a Shred Cube user.